
A growing solicitude; Cause and Effects in relation to Pakistan
The 21st century has witnessed mushroom growth in telecommunications, computing power and data processing technologies. Nowadays, electronic data processing is within reach of every individual, due to compact, powerful and cheap computing devices. Modern communication technologies like internet not only enable these devices to become globally connected with each other but also share their processed data and information in a very convenient manner. However this convenient and simple access to information has given birth to some vulnerability, one of them is the risk of theft and misuse of the valuable information.
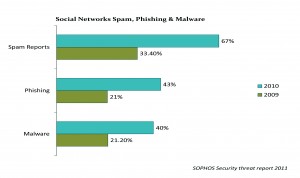
In year 2010, the global internet users have been increased to 1.97 billion generating astounding traffic of 294 billion emails per day, so far around 262 billion emails are found to be spam emails which are 89.1{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of the global email traffic. Similarly 662 data breaches have been recorded by identity theft resource centre, in which 51{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} breaches are related to the exposure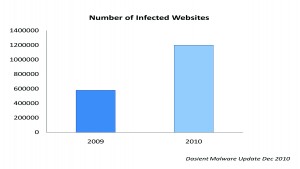 of valuable information regarding credit cards, bank accounts, national security numbers and other important records. Furthermore, a research study carried out by an IT security vendor shows a dramatic increase in web malware during the same year, the number of infected websites have reached 1.2 million which is 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} more as compared to previous year. In the same manner the users of social network services have also faced threats like phishing, spam and malwares via social network sites, according to a survey, an increase of 33.6{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in spam, 22{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in phishing and 18.8{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in malware via social network services have been observed during 2010 showing a fair rise of approximately 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} as compared to 2009.
of valuable information regarding credit cards, bank accounts, national security numbers and other important records. Furthermore, a research study carried out by an IT security vendor shows a dramatic increase in web malware during the same year, the number of infected websites have reached 1.2 million which is 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} more as compared to previous year. In the same manner the users of social network services have also faced threats like phishing, spam and malwares via social network sites, according to a survey, an increase of 33.6{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in spam, 22{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in phishing and 18.8{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} in malware via social network services have been observed during 2010 showing a fair rise of approximately 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} as compared to 2009.
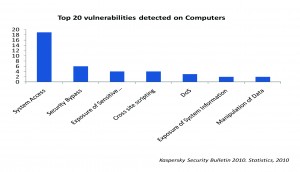 Moreover a research report from leading anti-virus developer also highlights some popular vulnerability found in modern computer system. The report states that around 19 out of every 20 vulnerability are the attempts of gaining unauthorized access to system operations, 6 out of those 19 attempts help hackers to bypass security systems and 4 out of those 19 attempts related to the acquisition of sensitive infor
Moreover a research report from leading anti-virus developer also highlights some popular vulnerability found in modern computer system. The report states that around 19 out of every 20 vulnerability are the attempts of gaining unauthorized access to system operations, 6 out of those 19 attempts help hackers to bypass security systems and 4 out of those 19 attempts related to the acquisition of sensitive infor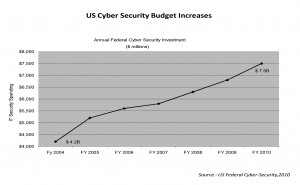 mation in the system.
mation in the system.
The outrageous facts of flaws in information security have compelled many countries to initiate drastic improvement in this sector. Several countries have started to boost up their funding in information security sector. In 2010 US alone has increased its cyber security budget from $6.8 Billion to $7.5 Billion, in which it has allocated $397 million for improving cyber security which is 27{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} more as compared to fiscal 2009.
allocated $397 million for improving cyber security which is 27{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} more as compared to fiscal 2009.
Nevertheless so far in Pakistan, the sector of information security has been left unattended. Numerous public & private sector organizations are facing losses due to information security threats. Therefore in order to project the current situation of information security within Pakistan, a survey has been conducted to analyze the global and local opinions regarding prominent factors like challenges for Information security, top IT risks, investment in Information security and countermeasures for Sensitive data leakages and IT threats.
1. Challenges for effective delivery of Information Security Initiatives
According to global prospective, 64{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have indicated that security awareness of the employees is quite a big challenge. Many organizations have serious concerns over un-intentional security breaches made by the employees, most of them believe that employees don’t have sufficient knowledge about security threats associated with advance devices like smart phones, handheld computers etc, therefore the solution is to provide proper IT security awareness trainings, but due to global economic recession, financially managing these trainings have became quite challenging task. Furthermore the said recession has also lowered down the availability of resources and funds causing a challenging situation as indicated by most of participants.
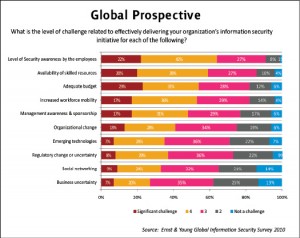 Moreover the increasing demand for information by the mobile workforce has also posed information security issues, many organizations are struggling to control the flow of information from mobile computing and see it as a significant challenge. Around 53{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have considered increased workforce mobility as noteworthy challenge towards the effective delivery of information security initiatives.
Moreover the increasing demand for information by the mobile workforce has also posed information security issues, many organizations are struggling to control the flow of information from mobile computing and see it as a significant challenge. Around 53{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have considered increased workforce mobility as noteworthy challenge towards the effective delivery of information security initiatives.
So far in Pakistan, the bad economic condition of the country has caused quite difficult situation for financing information security initiatives, 81{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have indicated that adequate budget is one of the major challenge towards the delivery of information security initiatives. Furthermore around 72{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants have highlighted that Business uncertainty is also significant challenge because day by day degrading security and economic conditions of the country have produced chaos situation for many businesses and most of them have ceased their further investments as indicated above. It also be noted the around 71{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have pointed out that regulatory change is also quite challenging. In Pakistan, the upper management of many organizations especially public sector organizations are not fairly aware about information security threats due to lack of vision and technological knowledge, therefore most of the time they show resistance in regulatory changes.
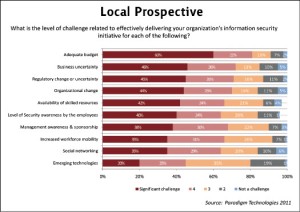
It has also been observed that the dreadful monetary condition has caused reduction of remuneration packages for several IT Security professionals, thus diminishing their motivations towards working in the country and has compelled them to go abroad for better pay packages. Therefore the availability of skilled resources has also become a noteworthy challenge towards the effective delivery of said initiative as identified by 70{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants.
2. Top IT risks for Organizations
It has been found that numerous organizations have made their systems automated and all of these systems are powered by critical IT infrastructure from the backend. These infrastructures are on the hit list of cyber criminals who paralyze them through their attacks, resulting in non-availability of IT resources for some valuable time. When the global survey participants have been asked to identify their top five areas of IT risks for their organization, most of them have indicated that the continuous availability of critical IT resources is one of the top most IT risks for their organization.
It has been also observed that the usage of mobile computing for business purposes have also increased, the serious risk associated with mobile devices is the risk of losing data (Sensitive information) through them due to theft or working in unsecure environment. Around 64{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participant have identified data as one of the top five IT risks in 2010. Similarly vulnerabilities in applications and databases also possess high security concerns, around 55{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have also quoted it as one of top five IT risks.
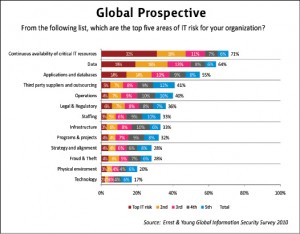 The local prospective exhibits a totally different picture as compared to global one. Majority of survey participants have identified legal and regulatory area as one of the top most IT risk for the organization because absence of proper regulatory and legal support for information security may cause difficulties in legally dealing with e-crimes and generate problems in enforcement of information security control measures.
The local prospective exhibits a totally different picture as compared to global one. Majority of survey participants have identified legal and regulatory area as one of the top most IT risk for the organization because absence of proper regulatory and legal support for information security may cause difficulties in legally dealing with e-crimes and generate problems in enforcement of information security control measures.
Similar to the global participants, around 86{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local survey participants have also placed continuous availability of critical IT resources as the second most prominent IT risk.
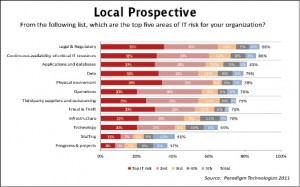 Security issues of databases like database communication protocol & platform vulnerabilities, weak authentication, backup data exposure and SQL injection, similarly security weakness of applications like malware, unauthorized access to system resources and Denial of Service have developed serious risks regarding security of applications and databases. 81{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have indicated it as one of top five IT risks. Furthermore the threat of losing sensitive data especially through mobile/portable devices has also created noteworthy risk for many organizations as indicated by 79{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants. It has also be noted that due to abruptly degrading security situation of Pakistan 78{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have chosen physical environment as one of the top five IT risks for their organization.
Security issues of databases like database communication protocol & platform vulnerabilities, weak authentication, backup data exposure and SQL injection, similarly security weakness of applications like malware, unauthorized access to system resources and Denial of Service have developed serious risks regarding security of applications and databases. 81{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have indicated it as one of top five IT risks. Furthermore the threat of losing sensitive data especially through mobile/portable devices has also created noteworthy risk for many organizations as indicated by 79{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants. It has also be noted that due to abruptly degrading security situation of Pakistan 78{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have chosen physical environment as one of the top five IT risks for their organization.
3. Investment in Information Security
In order to further enhance any sector, investment plays a vital role in its transformation. Therefore to know the organization’s plans for further investment in information security sector, a query regarding the said subject have been disseminated within the global survey participants. Survey results exhibit that despite of tight economic situation many organizations have planed to spend more money over the next year. Majority of organizations have analyzed the security issues associated with mobile computing, most of them have shown their serious concerns over the leakage of information through these devices. Therefore the top priority of most of the organizations is prevention of data leakages especially from mobile devices which can be judged by the survey results as 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have planned to spend more 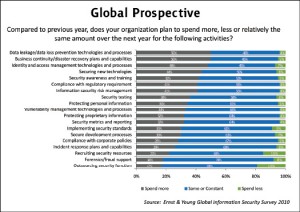 over the next year on data leakage/data loss prevention technologies and processes. Furthermore mobility and hurdles in controlling the end-user devices can cause hindrances in implementing effective and efficient business continuity and disaster recovery capabilities, 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of respondents have recognized this area for more funding.
over the next year on data leakage/data loss prevention technologies and processes. Furthermore mobility and hurdles in controlling the end-user devices can cause hindrances in implementing effective and efficient business continuity and disaster recovery capabilities, 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of respondents have recognized this area for more funding.
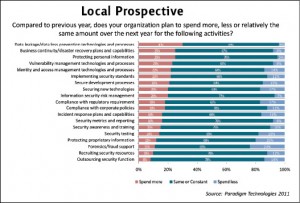 The survey results from Pakistan depicts that the many organizations are hit by the consequences of economic situation of the country, most of them are willing to spend same as they spend last year on information security. Likewise the global respondents, around 30{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have proposed increased funding in data leakage/loss prevention technologies and processes, similarly 25{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have shown keen interest in investing more on business continuity and disaster recovery capabilities. Security threats associated to abuse of personal information has also been realized by many of the respondents, around 25{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have planned to invest more in protecting personal information.
The survey results from Pakistan depicts that the many organizations are hit by the consequences of economic situation of the country, most of them are willing to spend same as they spend last year on information security. Likewise the global respondents, around 30{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have proposed increased funding in data leakage/loss prevention technologies and processes, similarly 25{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have shown keen interest in investing more on business continuity and disaster recovery capabilities. Security threats associated to abuse of personal information has also been realized by many of the respondents, around 25{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants have planned to invest more in protecting personal information.
4. Countermeasures for increasing IT Security Risk
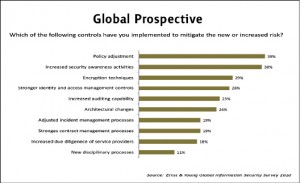
Observing the efforts taken by the organizations to address the potential new risks, it has been found that 39{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of global survey participants are making policy adjustments, 38{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} are increasing their security awareness activities, 29{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} are implementing encryption techniques and 28{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} are implementing stronger identity and access management controls. Survey results show that many respondents are keen to make and modify information security policies, in order to manage new technologies and information flow especially from mobile devices. Furthermore most of them have also focused on increasing security awareness trainings in order to educate employees about the usage and associated security risks regarding new emerging technologies and devices.
 The response from the local survey participants has shown that most of the organizations in Pakistan are showing keen interest in implementing stronger identity and access management controls for providing right access to right people, as indicated by 38{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants. 35{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants are implementing strong encryption techniques to ensure secure delivery of data over public networks.
The response from the local survey participants has shown that most of the organizations in Pakistan are showing keen interest in implementing stronger identity and access management controls for providing right access to right people, as indicated by 38{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants. 35{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants are implementing strong encryption techniques to ensure secure delivery of data over public networks.
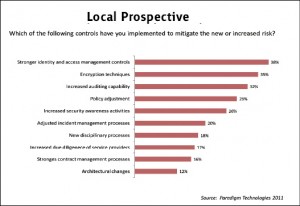 Furthermore 32{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants have been trying to increase IT security audit capability in order to ensure perfect working of IT security systems, observing the compliance of rules and procedures regarding information security and auditing both physical & logical IT security measures of the organization. Likewise global respondents around 29{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local participants are also making policy adjustments to further enhance their management capabilities for dealing with IT security risks.
Furthermore 32{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of participants have been trying to increase IT security audit capability in order to ensure perfect working of IT security systems, observing the compliance of rules and procedures regarding information security and auditing both physical & logical IT security measures of the organization. Likewise global respondents around 29{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local participants are also making policy adjustments to further enhance their management capabilities for dealing with IT security risks.
5. Controlling leakage of Sensitive Information
It has been observed that data leakage often caused due to careless attitude of employees who are unaware that their actions might cause leakage of sensitive information. A large portion of this issue is usually associated to absence of specific policy or inadequate awareness of policies. To address this issue, majority of organizations have developed specific policy for handling sensitive information as indicated by 73{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of global survey participants. Moreover around 65{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of respondents implemented additional security mechanism for protecting information in order to further enhance their existing countermeasures against the data leakage.
 Furthermore several organizations are keen to investigate their IT security systems in order to check the defense mechanism against information leakage and to ensure its perfect operations. In this context around 54{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of global respondents have utilized internal auditing for testing of controls in their organizations.
Furthermore several organizations are keen to investigate their IT security systems in order to check the defense mechanism against information leakage and to ensure its perfect operations. In this context around 54{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of global respondents have utilized internal auditing for testing of controls in their organizations.
Likewise the global surveys, around 75{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local survey participants have defined a specific policy for controlling the leakage of sensitive information. It has also been observed that the new generation employees are excessively utilizing the instant messaging and social networking services in their daily routine. Several organizations are experiencing difficulties in securing the flow of information through these services due to lack of awareness of employees and high cost of security software, therefore in order to control the leakage of information through the said services, numerous organizations have prohibited the use of instant messaging and social networking at their premises as indicated by 65{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of survey participants.
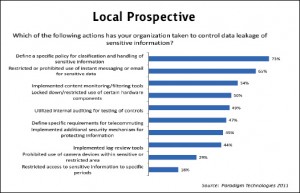 Furthermore nowadays employees also have access to huge amount of data for efficient business purpose but this advantage has a significant risk of exposure of information via various internet based services by the employees. So far the immediate solution to this problem is to restrict access to various web services but restricting the access will affect both business efficiency and attitude of the employees therefore the high-tech solution is the implementation of content monitoring and filtering system. Around 54{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local survey participants have implemented content monitoring/filtering tool in their organization, in order to analyze the flow of information for both legal & monitoring purposes and also for ceasing the dissemination of sensitive information, thus providing uninterrupted fair access to several web services like chats, email and social networking to the employees.
Furthermore nowadays employees also have access to huge amount of data for efficient business purpose but this advantage has a significant risk of exposure of information via various internet based services by the employees. So far the immediate solution to this problem is to restrict access to various web services but restricting the access will affect both business efficiency and attitude of the employees therefore the high-tech solution is the implementation of content monitoring and filtering system. Around 54{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} of local survey participants have implemented content monitoring/filtering tool in their organization, in order to analyze the flow of information for both legal & monitoring purposes and also for ceasing the dissemination of sensitive information, thus providing uninterrupted fair access to several web services like chats, email and social networking to the employees.
Key Findings
Comparative analysis of both global and local surveys depicts quite different picture. At few places the interests of both the global and local community are found to be similar but at several places there are contradictions.
In 2010, majority of global community considered the IT security awareness of employees and increase work force mobility as most significant challenges towards effect delivery of IT security initiative, whereas the local community has highlighted the un-availability of funds, skilled resources and effective regulatory changes are challenging obstacles towards the delivery of said initiative. Furthermore global participants have declared continuous availability of IT resources and sensitive data are prominent areas prone to IT risks whereas local participants have shown their concern over availability of proper legal & regulatory support, physical environment and applications & databases as top IT risks.
It was also noted that despite of unstable global economic situation, several global organizations have proposed to increase their funding for dealing with information security threats, but irrespective to global attitude, most of the local organizations have planned to stay constant regarding their expenditure towards information security.
Moreover during the last year, numerous global participants have been engaged in making adjustment in IT security policies, boosting up the awareness campaigns of employees and spending on advance encryption techniques for constructing stronger defense against IT risks, whereas in Pakistan, majority of local organizations were busy in implementing strong identity and access management system, enhancing their IT security audit capability and likewise the global community spending on advance encryption techniques in order to diminish the increased IT risks.
It was also noted that many global organizations have defined specialized policy and enhanced their security systems for controlling the leakage of sensitive information. Furthermore they have also utilized internal auditing mechanism for checking and ensuring their control system against said threat. Likewise in Pakistan, majority of local businesses have made the policy for controlling the exposure of sensitive information, but on other hand unlike the global trend, they have focused on restricting the access to email, chat and social networking services and also on implementing content monitoring and filtering systems to address the issue of leakage of sensitive data.
Conclusion
It has been observed that the IT security threats are exponentially increasing year by year. During 2010, around 50{e1f18614b95d3cd6e4b3128e1cd15d99b042a60a5a19c19b7a8e07e7495efa10} more information security incidents have been reported as compared to 2009. Therefore the global community has been very keen to address this issue and taking stronger steps for safeguarding the precious information and diminishing the increased IT security threats.
As far as Pakistan is concerned the scenario is quite different. Several organizations have ceased further investment in information security which undisputedly is imperative in its very nature. Furthermore the general masses are less convergent to IT security risks especially associated to mobile devices, social networking services and information handling; resulting in data breaches and loss of data. Moreover due to fair resistance in regulatory modification and absence of proper legal and regulatory support for dealing with information security threats, many IT security professionals are facing problems in legally handling the IT security incidents and managing strong defense against said incidents.
Therefore in order to make things better, local organizations should increase their investments in information security sector. They must begin conducting IT security awareness campaigns and seminars for employees especially addressing security threats associated to mobile computing and social networking. Furthermore they have to turn their focus towards establishing a clear “Information Security Policy” and adopt it as a strategy to mitigate risk. Moreover they should start adopting internationally recognized standards and frameworks for information security in order make their countermeasures up to the mark.
May 20, 2024















